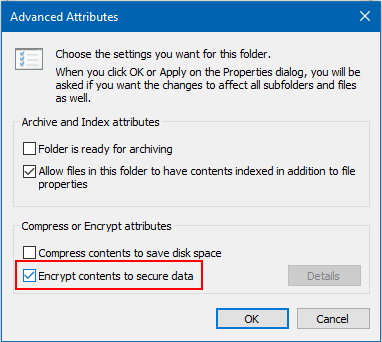
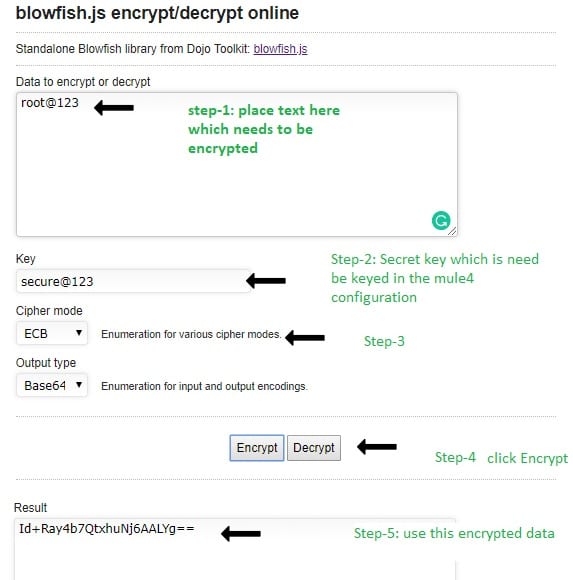
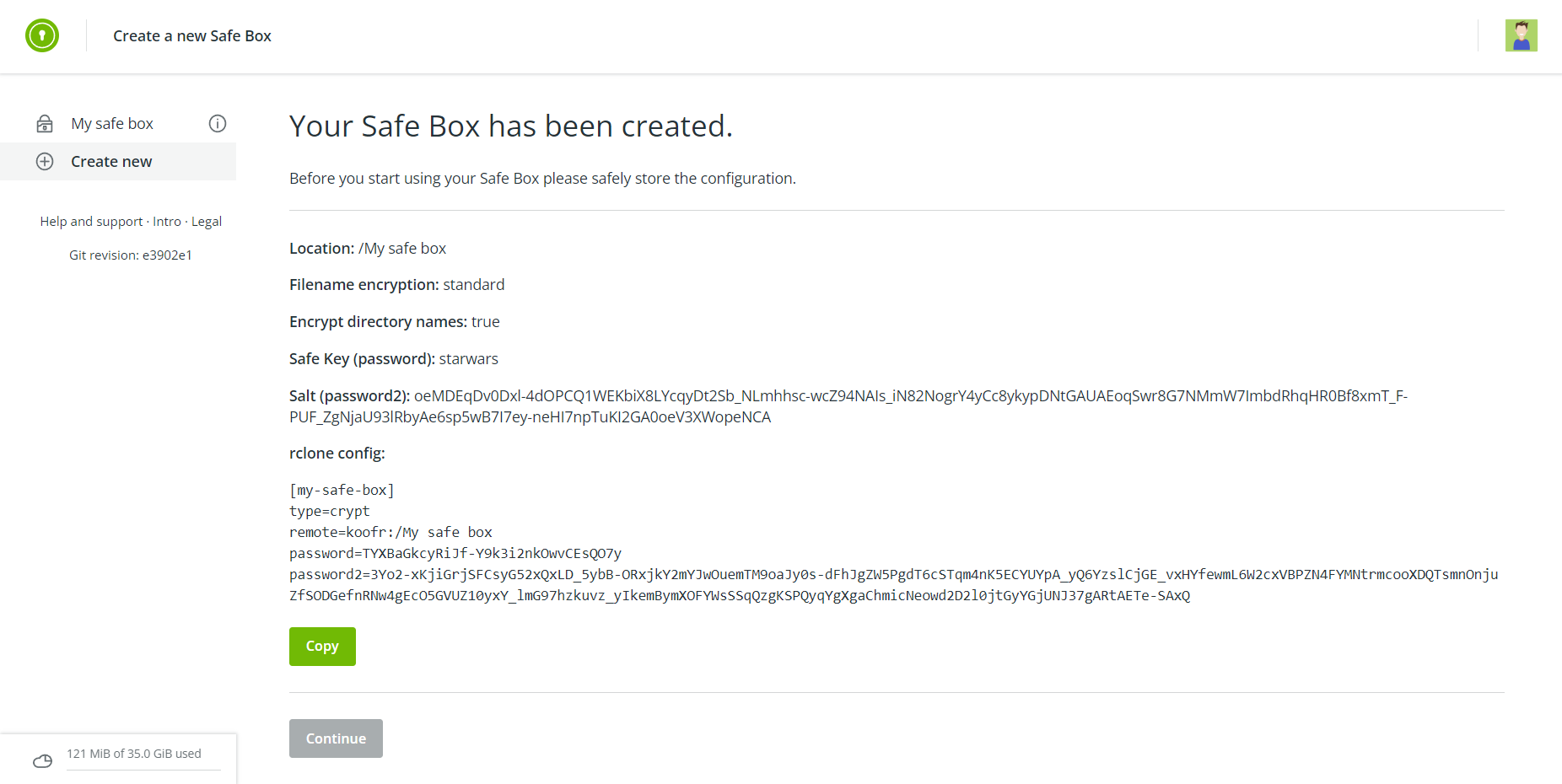
Computers | Free Full-Text | A Fast Text-to-Image Encryption-Decryption Algorithm for Secure Network Communication

LastPass finally admits: Those crooks who got in? They did steal your password vaults, after all… – Naked Security

Amazon.com: Wooden Jewelry Secret Puzzle Stash Box Case with Secret Compartment Lock hiden Key, Personal Secrets Storage Safe, Brain Teaser

Moc Diy Strongbox Mini Combination Safe Building Block Kit Decrypt Treasure Coffer Box Brick Model Kid Brain Puzzle Toy Gift - Blocks - AliExpress

Are Encrypted Lockboxes for Data Centers Worth the Usability Cost? | Data Center Knowledge | News and analysis for the data center industry